AWS Cost Explorer Policy: A Practical Guide For Managing Cloud Spending
Keeping a close watch on your cloud spending is, you know, absolutely essential in today's fast-paced digital world. Amazon Web Services (AWS) is, after all, the world’s most comprehensive and broadly adopted cloud, offering over 200 fully featured services from data centers globally. With so many powerful tools at your fingertips, it’s easy for costs to add up if you're not careful, and that's a common challenge for many organizations.
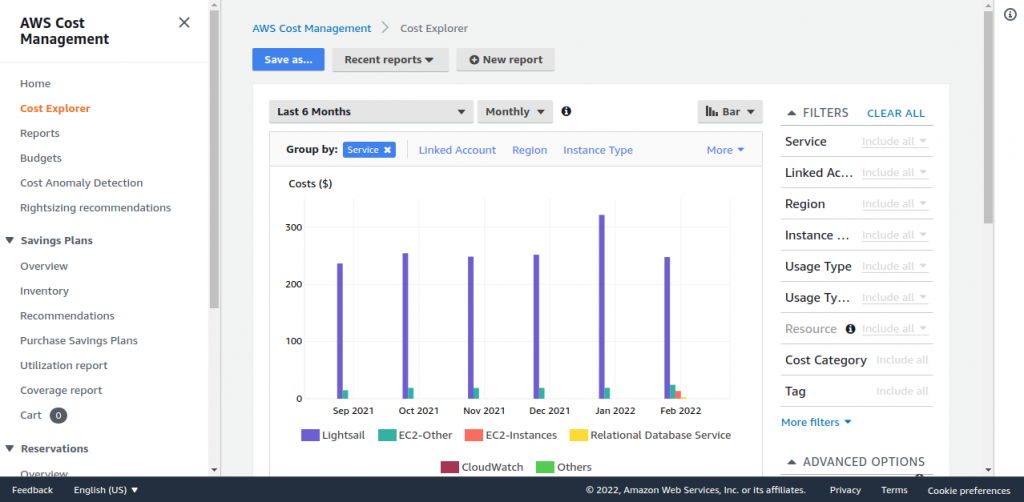
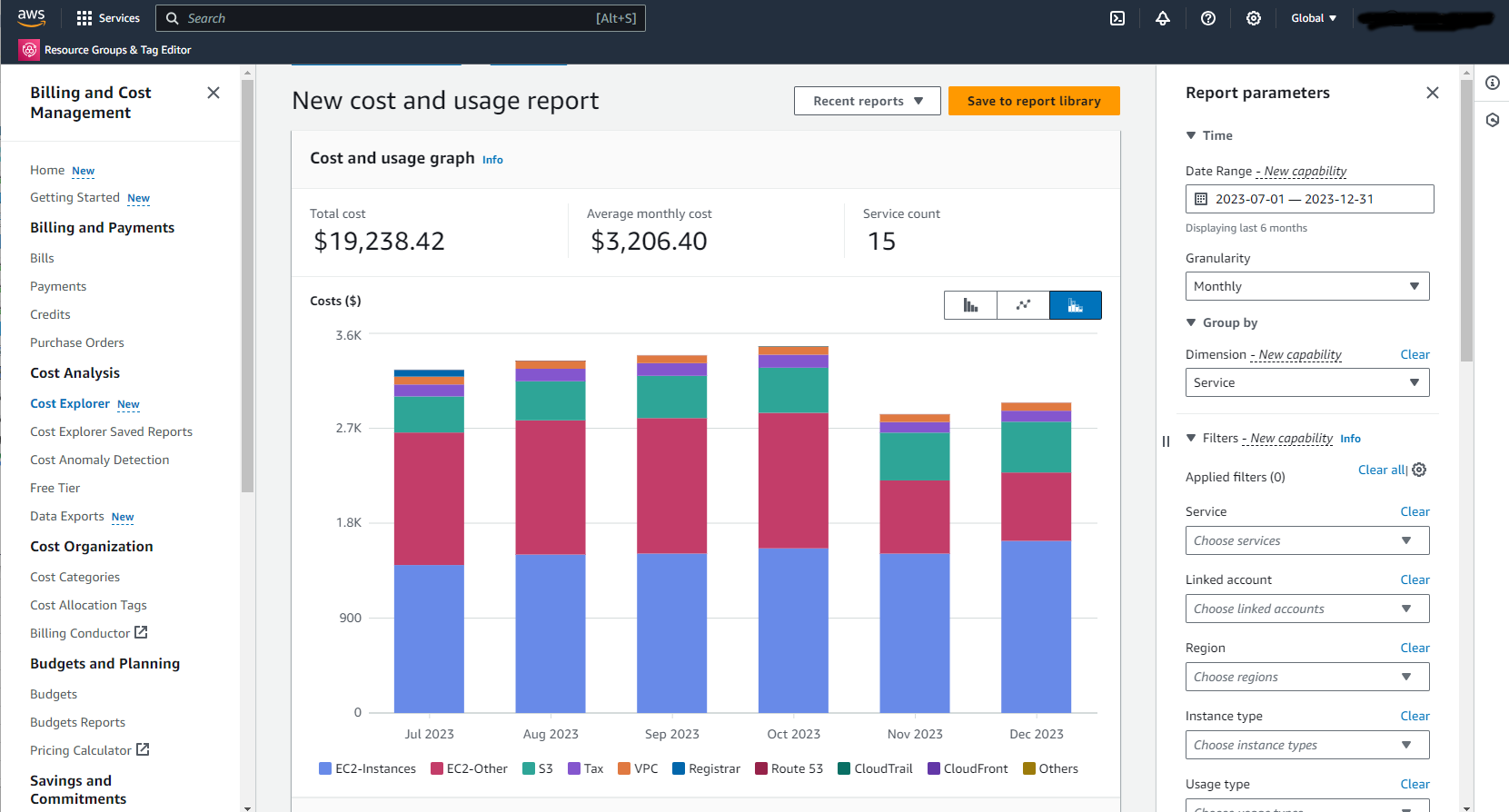
This is where AWS Cost Explorer really shines, actually. It's a fantastic service that helps you visualize, get a good grasp of, and even manage your AWS costs and usage over time. You can see what you're spending money on, spot trends, and find ways to save, which is pretty helpful.
But having a tool like Cost Explorer is only half the story, right? You also need to control who can actually see and mess with this sensitive financial data. That's precisely why understanding and setting up proper AWS Cost Explorer Policy rules is so very important for keeping your cloud finances secure and in order.
Table of Contents
- What Exactly is AWS Cost Explorer?
- Why You Need a Good AWS Cost Explorer Policy
- Getting to Grips with IAM and Cost Explorer Access
- Common Ways People Use Cost Explorer Policies
- Making Your Own AWS Cost Explorer Policy: A Step-by-Step Guide
- Good Habits for Managing Cost Explorer Access
- Connecting Cost Explorer Policies with Other AWS Tools
- Frequently Asked Questions (FAQs)
What Exactly is AWS Cost Explorer?
AWS Cost Explorer is a free tool that helps you see your AWS spending patterns. It's like a financial dashboard for your cloud usage, you know, making sense of all those numbers. You can view data for the last 13 months, forecast future spending for up to 12 months, and get suggestions for potential savings. It’s pretty useful for anyone looking to keep their cloud budget in check.
How it Helps with Cloud Spending
This service lets you get a clear picture of where your money is going within AWS. You can break down costs by service, resource, or even by specific tags you've applied, which is rather handy. For instance, if you're using AWS for machine learning, you'll appreciate that AWS offers the best price performance for machine learning training, as well as the lowest cost per inference instances in the cloud. Cost Explorer helps you see those savings in action, or find areas where you could be saving more.
Many businesses find the AWS pricing calculator a really helpful way to explore AWS services and create an estimate for the cost of their use cases on AWS. Once things are running, Cost Explorer picks up the job of showing you the actual spending against those estimates. It’s a great way to stay informed about your financial picture, you know, in real-time almost.
Why You Need a Good AWS Cost Explorer Policy
Just like you wouldn't leave your physical financial records lying around for anyone to see, you shouldn't do that with your cloud spending data either. A good AWS Cost Explorer Policy is like a security guard for your financial information in the cloud. It makes sure only the right people can look at or change your cost reports, which is pretty important for security.
Keeping Your Financial Data Safe
AWS is architected to be the most flexible and secure cloud computing environment available today, with infrastructure built to satisfy the security requirements of the highest sensitivity. This commitment to security extends to your billing and cost data, too. A well-crafted policy helps protect sensitive financial information from unauthorized eyes, which could be internal or external. It prevents accidental changes or even intentional misuse of your cost data, you know, keeping everything sound.
Making Sure People Only See What They Should
Different people in your organization have different jobs, and that means they need different levels of access to information. Your finance team might need to see everything, but a developer might only need to see the costs related to their specific project, for example. Policies let you set these boundaries, so everyone gets just the right amount of information without being overwhelmed or seeing things they shouldn't, which is really quite useful.
Getting to Grips with IAM and Cost Explorer Access
To really get a handle on AWS Cost Explorer policies, you need to understand AWS Identity and Access Management (IAM). IAM is the system AWS uses to manage who can do what in your AWS account. It’s the gatekeeper for all your AWS services, so it's a big deal.
What IAM Does for AWS
IAM helps you manage users, groups, and roles, and then attach policies to them. These policies are essentially documents that say "this person can do X, Y, and Z, but not A, B, or C." It's how you make sure your cloud environment stays secure and organized, which is, you know, a very good thing. You can understanding AWS IAM more deeply on our site.
The Actions You Can Control
When it comes to Cost Explorer, there are specific actions you can allow or deny within an IAM policy. These actions usually start with `ce:` (for Cost Explorer). For example, `ce:GetCostAndUsage` lets someone retrieve cost and usage data. `ce:GetReservationUtilization` gives access to reservation utilization reports. There are many such actions, and you pick the ones that match what each user needs to do, which is rather precise.
It’s important to remember that some actions, like `ce:CreateCostCategoryDefinition` or `ce:UpdateCostCategoryDefinition`, allow changes to how costs are grouped. These are often considered more sensitive and should be given out very sparingly, so you know, be careful with them.
Common Ways People Use Cost Explorer Policies
People use Cost Explorer policies in several common ways, depending on what their team members need to do. It’s all about fitting the access to the job, really.
Giving Just Viewing Rights
The most common setup is giving users read-only access. This means they can look at all the reports, see the spending, and analyze the data, but they can't change anything. This is perfect for most developers, project managers, or even some budget analysts who just need to monitor costs, you know, without making any alterations. A policy for this would include actions like `ce:GetCostAndUsage`, `ce:GetDimensionValues`, and `ce:GetRightsizingRecommendation`.
Letting Some People Do More
Certain roles, like a FinOps specialist or a senior financial controller, might need to do more than just view. They might need to create cost categories, set up budgets (which integrates with Cost Explorer), or even manage reservations. For these roles, you'd add more permissions, such as `ce:CreateCostCategoryDefinition` or `ce:UpdateCostCategoryDefinition`. This allows them to actively shape how costs are presented and managed, which is pretty powerful.
Controlling Access for Specific Projects
One very useful thing you can do is limit access based on tags. AWS lets you add tags (like "Project: Alpha" or "Department: Marketing") to your resources. With a policy, you can say, "this user can only see Cost Explorer data for resources that have the tag 'Project: Alpha'." This is fantastic for large organizations where different teams manage their own budgets, you know, keeping things separate. It helps keep things tidy and focused for each team.
Making Your Own AWS Cost Explorer Policy: A Step-by-Step Guide
Creating an AWS Cost Explorer policy might seem a bit tricky at first, but it's really a structured process. You'll work with JSON documents that tell AWS exactly what to allow or deny. It’s like writing a very specific set of instructions, so you know, pay attention to the details.
Starting with a Basic Template
You usually begin with a basic IAM policy template. AWS provides some managed policies, like `ReadOnlyAccess` or `Billing`, that you can adapt. For Cost Explorer, a good starting point for read-only access looks something like this (remember, this is just an example):
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "ce:GetCostAndUsage", "ce:GetCostAndUsageWithResources", "ce:GetDimensionValues", "ce:GetTags", "ce:GetRightsizingRecommendation", "ce:GetReservationUtilization", "ce:GetReservationPurchaseRecommendation", "ce:GetReservationCoverage", "ce:GetSavingsPlansUtilization", "ce:GetSavingsPlansPurchaseRecommendation", "ce:GetSavingsPlansCoverage" ], "Resource": "*" } ] } This policy, you know, pretty much gives full viewing access to Cost Explorer data. You can then adjust it from there.
Adding Permissions Carefully
If someone needs to do more than just view, you'll add specific `ce:` actions to the `Action` list. For example, to allow someone to create a cost category definition, you'd add `ce:CreateCostCategoryDefinition`. Always try to add the fewest permissions needed for the job, you know, that's a really good rule to follow. This approach helps keep your account secure and follows the principle of least privilege.
For more advanced controls, like restricting access based on tags, you'd add a `Condition` block to your policy. This is where you specify that the action is only allowed if a certain tag is present on the resource or in the request context. It's a slightly more advanced step, but very powerful for granular control, actually.
Trying Out Your New Policy
After you create a new policy, it's a good idea to test it out. You can attach it to an IAM user or role and then try to access Cost Explorer. See if they can do everything they're supposed to, and more importantly, if they *can't* do things they shouldn't. AWS provides tools like the IAM Policy Simulator that can help you understand what a policy allows or denies before you even deploy it, which is, you know, very helpful for avoiding mistakes.
Good Habits for Managing Cost Explorer Access
Setting up policies is one thing, but keeping them effective over time requires some good habits. Cloud environments change, and so do team roles, so staying on top of your policies is pretty important.
Always Give the Least Amount of Access
This is a golden rule in cloud security: always give the minimum permissions necessary for a user or service to do its job. Don't give full administrator access to someone who only needs to view cost reports, for example. This greatly reduces the risk of accidental errors or security problems, you know, keeping things tight. It's a simple idea, but it makes a big difference.
Checking Policies Often
It's a good practice to review your IAM policies regularly, maybe every few months or when team roles
AWS Cost Explorer - Control your AWS cost and usage time! - Cloudkul

Cloud Cost Analysis - AWS Cost Explorer - AWS
Cost Explorer - Learn / AWS