Boosting Your Cloud Security: What S3 PrivateLink Means For Data Access
Keeping your valuable data safe and sound in the cloud is, actually, a top concern for just about everyone these days. When you rely on services like Amazon S3 for storing all sorts of files—photos, audio, videos, and more, as our reference text mentions—you really want to make sure access is super secure. S3, as you know, is a simple storage service in AWS that stores files as objects, providing a lot of scalability and security. It is, more or less, the storage service of choice for many, especially when building a data lake. But what if you need to connect to S3 without ever touching the public internet? That's where something pretty cool comes into play, a service that changes how we think about secure connections to our cloud storage.
You see, Amazon S3, which gets its name from "Simple Storage Service," is basically the most fundamental storage building block of AWS's cloud offerings. It lets you store and retrieve any amount of data, and it is, quite frankly, ideal for things like data lakes, mobile applications, backups, archives, and even IoT projects. All your digital stuff goes into S3 buckets, and you can keep it organized with shared names called prefixes. But traditionally, when your applications or users talk to S3, that traffic often goes over the public internet, even if it's encrypted. This can be, in some respects, a point of concern for those with very strict security or compliance rules.
So, to address this, there's a really smart solution called S3 PrivateLink. It allows you to connect to S3 directly from your private network, completely bypassing the internet. This means your data traffic stays within the AWS network, making it, you know, a much more controlled and secure path. It's a way to make sure your interactions with S3 are as locked down as they can possibly be, offering a new level of confidence for your cloud operations. We'll explore this further, actually, as of our last update on July 29, 2025.
Table of Contents
- What is S3 PrivateLink?
- Why Use S3 PrivateLink? The Big Benefits
- How S3 PrivateLink Works Its Magic
- Getting Started: Setting Up S3 PrivateLink
- PrivateLink vs. Gateway Endpoint: What's the Difference?
- Real-World Scenarios for S3 PrivateLink
- Things to Think About Before You Start
- Frequently Asked Questions
- Final Thoughts on Secure S3 Access
What is S3 PrivateLink?
At its core, S3 PrivateLink is a network feature that lets you connect your Amazon Virtual Private Cloud (VPC) to S3 using a private endpoint. Think of it like creating a dedicated, private road directly from your network to S3, rather than using the public highway. This private connection means your data doesn't travel across the public internet at all. It stays entirely within the AWS network, which is, honestly, a pretty big deal for security. Our reference text notes that Amazon S3 is the largest and most performant object storage service, and PrivateLink just makes accessing it even more secure.
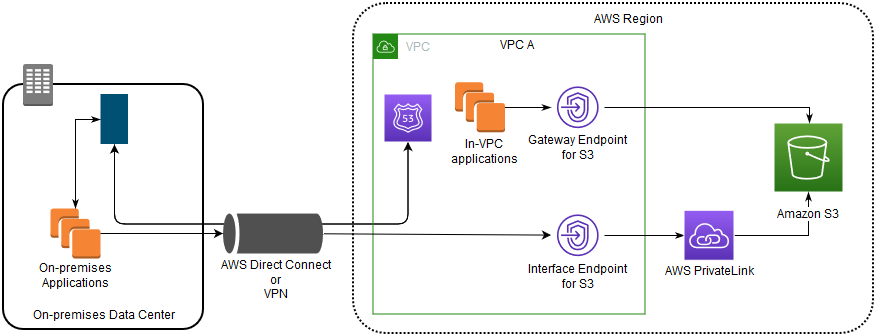
This service uses something called a VPC endpoint, specifically an interface endpoint, which is powered by AWS PrivateLink technology. When you set this up, you get private IP addresses in your VPC that serve as entry points for S3. So, any traffic meant for S3 from your VPC or even from your on-premises network (if you've got a Direct Connect or VPN connection to your VPC) goes straight to these private IPs. It's, you know, a really direct path.
It is, in a way, a solution that brings S3 closer to your applications, making the connection more predictable and secure. This approach is, quite frankly, a significant step up for many organizations that need to meet strict regulatory requirements or simply want to minimize their exposure to the public internet. It's all about keeping things private, basically.
Why Use S3 PrivateLink? The Big Benefits
There are several compelling reasons why folks are, you know, really excited about S3 PrivateLink. These benefits often address some pretty common pain points when it comes to cloud storage.
Enhanced Security and Compliance
The most obvious benefit is, arguably, security. By keeping all your S3 traffic off the public internet, you significantly reduce the attack surface. This is a huge win for compliance frameworks that require data to remain within a private network. For industries with strict regulations, like finance or healthcare, this feature is, actually, nearly essential. It helps you meet those tough requirements, basically.
When your data stays within the AWS network, it benefits from AWS's robust security infrastructure without the added risks that come with public internet routing. This means, you know, fewer worries about data interception or other external threats. It's a layer of protection that many find incredibly reassuring.
Improved Network Performance and Reliability
Private connections often mean more consistent and predictable network performance. Because your traffic isn't subject to the variable conditions of the public internet, you can expect lower latency and higher throughput when accessing S3. This is, you know, pretty important for applications that need fast, reliable access to large amounts of data.
For example, if you're running analytics workloads that pull data from S3, or if you have applications that frequently write to S3, a private connection can make a noticeable difference. It is, in some respects, like having a dedicated express lane for your S3 traffic.
Simplified Network Architecture
With S3 PrivateLink, you don't need to set up complex firewall rules or routing configurations to allow access to S3. The VPC endpoint handles the routing internally. This simplifies your network design, making it easier to manage and, you know, less prone to configuration errors. It's a cleaner way to connect, really.
You also don't need to use NAT gateways or proxy servers within your VPC to reach S3, which can save you money and reduce operational overhead. This is, quite frankly, a pretty big win for streamlining your cloud setup.
Consistent IP Addresses
The interface endpoints provide stable, private IP addresses within your VPC. This consistency can be, you know, really helpful for applications or systems that rely on fixed network addresses. It offers a more predictable environment for your cloud resources.
How S3 PrivateLink Works Its Magic
So, how does this private connection actually happen? It's, honestly, pretty clever. When you set up S3 PrivateLink, you're essentially creating an interface VPC endpoint for S3.
This interface endpoint creates Elastic Network Interfaces (ENIs) with private IP addresses in the subnets you choose within your VPC. These ENIs serve as the entry points for S3 within your private network. When your applications in the VPC try to access S3, the traffic is, you know, automatically routed to these private ENIs.
The DNS resolution for S3 also gets a little tweak. When you create the endpoint, AWS provides a specific DNS name for it. If you enable private DNS for the endpoint, queries for the public S3 service names (like `s3.us-east-1.amazonaws.com`) will, actually, resolve to the private IP addresses of the endpoint within your VPC. This means your applications don't need to change how they address S3; the magic happens behind the scenes.
This setup ensures that all communication with S3 stays within the AWS backbone network, never touching the public internet. It's a very secure and efficient way to handle data transfers, basically.
Getting Started: Setting Up S3 PrivateLink
Setting up S3 PrivateLink involves a few steps, but it's, honestly, not overly complicated. You'll primarily use the AWS Management Console, AWS CLI, or AWS SDKs, as our reference text mentions for working with Amazon S3.
Create an Interface VPC Endpoint: You'll start by going to the VPC console and creating a new endpoint. You'll choose "AWS services" and then find "S3" (specifically, the one for "com.amazonaws.region.s3" that indicates an interface endpoint, not a gateway endpoint). You'll need to select the VPC where you want the endpoint to reside.
Select Subnets: Choose the subnets within your VPC where you want the endpoint's ENIs to be created. It's a good idea to pick subnets in different Availability Zones for high availability, you know, just in case.
Configure Security Groups: Attach a security group to the endpoint. This security group should allow inbound traffic on TCP port 443 (HTTPS) from your VPC's resources that need to access S3. This is, pretty much, a standard practice.
Enable Private DNS Names: Make sure to enable "Enable DNS name" for the endpoint. This will, as a matter of fact, automatically route S3 DNS requests from your VPC to the private endpoint.
Attach an Endpoint Policy: You can attach an endpoint policy to control which S3 actions are allowed through this specific endpoint and which IAM principals can use it. This gives you, actually, very granular control over access.
Once the endpoint is created, your applications configured to use S3 from within that VPC will automatically start using the private connection. It's a pretty seamless transition, you know.
PrivateLink vs. Gateway Endpoint: What's the Difference?
This is, you know, a common question, and it's an important distinction. Before S3 PrivateLink, the only way to privately access S3 from a VPC was through a Gateway Endpoint.
A **Gateway Endpoint** is a route table entry that points to S3. It allows your VPC to access S3 without using an internet gateway or NAT device, but it's a "gateway" type endpoint, not an "interface" type. This means it doesn't create ENIs with private IPs in your subnets. It's, basically, a routing mechanism.
Here's why S3 PrivateLink (an interface endpoint) is, arguably, a step up in many situations:
On-Premises Access: Gateway endpoints only work for resources *within* the VPC where they're configured. They don't extend to on-premises networks connected via Direct Connect or VPN. S3 PrivateLink, however, does. You can, you know, connect your on-premises data centers to S3 privately through your VPC's interface endpoint.
Cross-VPC Access: Similarly, gateway endpoints don't support access from peered VPCs or through Transit Gateway. Interface endpoints, on the other hand, do. This makes S3 PrivateLink much more flexible for complex network architectures, which is, honestly, a huge advantage.
Consistent DNS: With PrivateLink, the standard S3 DNS names resolve to private IPs. Gateway endpoints, sometimes, require more specific DNS configurations or S3 bucket policies to ensure traffic routes correctly. PrivateLink is, in some respects, more straightforward for applications.
So, while gateway endpoints are still useful for simple in-VPC S3 access, S3 PrivateLink provides a much broader range of connectivity options, especially for hybrid cloud setups and multi-VPC environments. It's, you know, a more versatile tool in your networking toolkit.
Real-World Scenarios for S3 PrivateLink
Let's look at a few situations where S3 PrivateLink really shines.
Hybrid Cloud Architectures
Many organizations have data and applications both on-premises and in AWS. Connecting on-premises servers to S3 through a Direct Connect or VPN connection to a VPC with an S3 PrivateLink endpoint means your on-premises data can, actually, flow directly and privately to S3. This is, you know, ideal for backups, data synchronization, or moving large datasets without exposing them to the internet.
Highly Regulated Industries
For sectors like finance, healthcare, or government, strict compliance rules often dictate that data cannot traverse the public internet. S3 PrivateLink helps meet these requirements by ensuring all S3 traffic remains within the AWS private network, which is, quite frankly, a critical capability.
Multi-VPC and Shared Services Environments
In larger organizations, you often have multiple VPCs, perhaps for different departments or applications. If these VPCs need to access a central S3 bucket, S3 PrivateLink can provide a private, consistent way for all of them to connect, even if they're peered or connected via AWS Transit Gateway. This simplifies routing and security policies across your cloud footprint, basically.
Data Lakes and Analytics
Our reference text points out that S3 is the storage service of choice for building a data lake. When you have large-scale data analytics platforms in your VPCs processing vast amounts of data stored in S3, PrivateLink ensures that the data transfer is fast, reliable, and secure. This is, you know, very important for maintaining performance and data integrity during intensive operations.
Things to Think About Before You Start
While S3 PrivateLink offers some pretty compelling advantages, there are, you know, a few things to keep in mind.
Cost Considerations
AWS PrivateLink endpoints incur costs based on the number of ENIs provisioned and the amount of data processed through them. It's important to understand the pricing model and estimate your usage to avoid, actually, any surprises. This is, pretty much, a standard part of cloud planning.
Regional Availability
S3 PrivateLink is available in many AWS regions, but it's always a good idea to check the latest AWS documentation to confirm availability in your specific region. This is, you know, just good practice.
Monitoring and Logging
You should set up monitoring for your VPC endpoints using AWS CloudWatch and log network traffic using VPC Flow Logs. This helps you keep an eye on usage, performance, and any potential issues, which is, honestly, nearly essential for any production environment.
Learn more about secure cloud connections on our site, and link to this page AWS PrivateLink documentation.
Frequently Asked Questions
What is the difference between S3 PrivateLink and a Gateway Endpoint?
S3 PrivateLink (an interface endpoint) uses Elastic Network Interfaces with private IP addresses in your VPC, allowing private access to S3 from your VPC, peered VPCs, Transit Gateway, and even on-premises networks. A Gateway Endpoint, on the other hand, is a route table entry that provides private access only from within the VPC where it's configured, and it doesn't extend to on-premises or cross-VPC connections. S3 PrivateLink is, in a way, much more versatile.
How do I configure S3 PrivateLink?
You configure S3 PrivateLink by creating an interface VPC endpoint for S3 in your desired VPC. This involves selecting subnets, attaching security groups to control access, and enabling private DNS names so that S3 requests automatically resolve to the private endpoint. You can, actually, do this through the AWS Management Console, CLI, or SDKs.
What are the security benefits of using S3 PrivateLink?
The main security benefit is that all traffic to S3 stays entirely within the AWS private network, completely bypassing the public internet. This significantly reduces the attack surface, helps meet strict compliance requirements, and provides a more controlled and secure path for your data. It's, you know, a very robust security enhancement.
Final Thoughts on Secure S3 Access
Embracing S3 PrivateLink is, honestly, a pretty smart move for organizations that value data security, network performance, and simplified cloud architecture. It provides a dedicated, private pathway to your S3 buckets, ensuring your data remains protected and
AWS PrivateLink for Amazon S3 - Amazon Simple Storage Service

AWS PrivateLink for Amazon S3 is Now Generally Available - Datafoam

AWS PrivateLink for Amazon S3を分かりやすく解説してみる - サーバーワークスエンジニアブログ