Understanding Your Network: Tailscale Vs WireGuard For Secure Access
Getting your devices to talk to each other securely, especially when they are spread out, can feel like a real puzzle, you know? Whether you are trying to reach a server at home from a coffee shop or connecting a remote team, a secure network connection is pretty much essential these days. For many folks, the choice often comes down to two big names: Tailscale and WireGuard. Each one offers a way to build a private network over the internet, but they go about it in rather different ways, which is something we'll look at. This comparison will help you figure out which one might be the better fit for your specific needs, so you can make a good choice.
You might be wondering, "Why do I even need something like this?" Well, imagine trying to access files on your home server while you're traveling, or maybe you're running a small business and need your team to securely connect to internal tools without too much fuss. These tools, Tailscale and WireGuard, provide a kind of virtual private network, or VPN, that makes your devices act like they are all on the same local network, even when they're miles apart. This really helps keep your data safe and sound, as a matter of fact.
Deciding between these two can be a bit tricky because they both offer strong security and good performance, but their setup and ongoing management experiences are quite distinct. One might be super simple to get going, while the other gives you more fine-grained control, which could be important for some people. We'll explore these differences, looking at how they work, what makes them special, and what sorts of situations each one truly shines in, just to give you a clear picture.
Table of Contents
- What is WireGuard?
- What is Tailscale?
- Setup and Ease of Use: Getting Connected
- Network Architecture and Control
- Security and Authentication
- Advanced Features and Integrations
- Performance Considerations
- When to Choose WireGuard
- When to Choose Tailscale
- Frequently Asked Questions
What is WireGuard?
WireGuard is a fairly modern, incredibly fast, and very simple VPN protocol that aims to be much easier to set up and manage than older options like OpenVPN or IPSec. It uses strong, current cryptography, and its codebase is quite small, which makes it easier to audit for security flaws, which is a big plus. It's essentially a foundational piece of technology that you build upon, giving you the building blocks for your own secure network. You, like your, configure each connection manually, defining which devices can talk to which, and that's how it works.
What is Tailscale?
Tailscale, on the other hand, is a commercial product that builds upon WireGuard, making it much more user-friendly and feature-rich. It handles the complex key exchange and network configuration automatically, creating what's called a "mesh VPN." This means every device on your Tailscale network can talk directly to every other device, without needing to go through a central server, which is pretty neat. It ties into your existing identity provider, like Google or Microsoft, to manage who can access what, making it very easy for teams to use, too.
Setup and Ease of Use: Getting Connected
The initial setup process is, arguably, one of the biggest differences between these two options. One requires a hands-on approach, while the other takes care of most of the heavy lifting for you. This can really influence your decision, especially if you're not super comfortable with command lines or network configurations, you know?
WireGuard Setup: The DIY Approach
Setting up WireGuard typically involves generating public and private keys for each device you want to connect. Then, you manually exchange these public keys between your devices, creating a configuration file for each one. This file tells each device about its peers, their public keys, and the IP addresses they should use. It gives you complete control, which is great for those who like to tinker, but it can be a bit time-consuming, especially with many devices. You're basically building your network from the ground up, in a way.
For example, if you're setting up a server and a client, you'd generate a key pair on the server and another on the client. Then, you'd add the client's public key to the server's configuration and the server's public key to the client's configuration. You also need to manage firewall rules to allow the WireGuard traffic through. This process, while giving you lots of say, does require a good grasp of networking fundamentals, as a matter of fact.
Tailscale Setup: The Zero-Config Way
Tailscale simplifies this dramatically. Instead of manual key exchange, you just install the client software on your devices and log in with your identity provider. Tailscale then handles all the key generation, exchange, and firewall configuration automatically. It connects your devices into a secure mesh network without you having to touch a single configuration file. This "zero-config" approach is, very, appealing for individuals and teams who want to get up and running quickly without needing deep networking knowledge.
The process often starts with creating an authentication key through your Tailscale account, which is pretty straightforward. As mentioned in my own experience, "Before installing tailscale in truenas, create an auth key through your tailscale account." This key helps your devices join your private network securely. Once you have that, the rest is mostly automated. It's almost like magic how quickly your devices connect, actually.
Tailscale on TrueNAS: A Practical Example
Many people use network-attached storage (NAS) systems like TrueNAS for their home labs or small businesses. Setting up secure access to these can be a common challenge. My own experience with "How to setup tailscale on truenas scale to setup the tailscale app on my truenas" highlights how Tailscale streamlines this. After getting your authentication key, you can usually find the Tailscale app directly within the TrueNAS apps section. This makes adding your NAS to your secure network quite simple, basically.
Once installed, the TrueNAS system becomes another node on your Tailscale network, making it accessible from any other authorized device. This is a huge convenience for managing your files or services on the NAS remotely, without needing to open ports on your router or deal with complex VPN server setups. It just works, allowing you to access whatever app you have on your LAN via the usual IP and port, which is very helpful.
Network Architecture and Control
The way these two tools build and manage your network is another key difference, affecting how much control you have and how your devices communicate. This really influences how flexible your setup can be and what kind of network topology you can create, you know.
Peer-to-Peer with WireGuard
WireGuard itself is a peer-to-peer protocol. This means you establish direct connections between individual devices. If you have five devices, and you want them all to talk to each other, you'd typically set up a star topology where each client connects to a central WireGuard server. Or, you could configure a full mesh, where each device has a direct connection to every other device, which can become quite complex to manage as your network grows, as a matter of fact.
The beauty of WireGuard here is its simplicity at the protocol level. It's just about secure tunnels between two points. Any routing or network discovery beyond that is something you have to implement yourself, using your operating system's networking tools. This level of control is often preferred by those with specific network requirements or who want to avoid any third-party services for their core network connections, in a way.
Mesh Network with Tailscale
Tailscale, by contrast, creates a "mesh" network automatically. Every device on your Tailscale network can talk directly to every other device, given the right permissions. It uses a coordination server to help devices find each other (a process called NAT traversal), but once they've found each other, the traffic flows directly between them using WireGuard. This means there's no central bottleneck for your data, which is pretty good for performance, too.
This mesh approach makes adding new devices or services very easy. You don't need to reconfigure existing devices; the new one just joins the mesh. It's especially useful for dynamic environments or when you have many devices that need to communicate with each other without a single point of failure. The coordination server is, very, critical for the initial connection, but not for the ongoing data transfer.
Subnet Routing and DNS Queries
Both solutions can handle subnet routing, allowing you to access entire local networks through a single device on your secure network. With WireGuard, you configure this manually by adding routes to your configuration files. With Tailscale, you can advertise entire LAN subnets to your Tailscale network, as my experience shows: "Configure your tailscale server on the lan to advertise the entire lan subnet to tailscale, then you can just access whatever app you have on your lan via the usual ip and port." This means you can reach all your local devices, like printers or other servers, through just one Tailscale device acting as a gateway.
DNS handling is another interesting point. Tailscale provides its own DNS resolution, which can be quite convenient for accessing services by name rather than IP address. However, as I've seen, "Using tailscale dns query the long address resolves, But using nslookup it does not, The short address fails on both." This sometimes means you might need to adjust your expectations or troubleshoot specific DNS behaviors depending on how you're trying to resolve names. It's a subtle point that can affect how you interact with services, you know.
Security and Authentication
Security is, arguably, the most important aspect of any VPN solution. Both WireGuard and Tailscale are built on strong cryptographic principles, but their approaches to authentication and access control differ significantly.
WireGuard Security: Keys and Configuration
WireGuard's security relies purely on cryptographic keys. Each device has a unique private key, and it shares its public key with its peers. This means that if you have the correct public key for a peer, you can communicate securely with it. The challenge here is managing these keys securely. You need to ensure keys are generated properly, stored safely, and exchanged without compromise. There's no central identity provider; it's all about those keys, as a matter of fact.
Access control with WireGuard is also managed through these keys and your network configuration. If a device has the correct key and is listed as a peer, it can connect. This offers a very high degree of privacy and control, but it also means you're responsible for all aspects of key management and access policies. For a small number of devices, this is fine, but it can get tricky with many connections, which is something to consider.
Tailscale Security: Identity and Access Control
Tailscale takes a different path by integrating with existing identity providers (like Google Workspace, Microsoft Entra ID, or Okta). When you log into Tailscale, it uses your existing identity to authenticate you. This means that your users' access to your private network is tied to their existing corporate or personal accounts. This makes managing user access much simpler, especially for teams, you know.
Access control in Tailscale is handled through an access policy file, often called an ACL (Access Control List). This file, which you manage in your Tailscale account, defines which users or groups can access which devices or services on your network. It allows for very granular control, letting you say, for instance, that only members of the "developers" group can access the "staging server." This approach, really, reduces the burden of key management while offering strong, identity-based security.
Advanced Features and Integrations
Beyond basic connectivity, both solutions offer ways to extend their usefulness, though Tailscale tends to have more built-in features and integrations due to its managed nature.
Docker and Automation with Tailscale
For those who use Docker, Tailscale offers very flexible deployment options. My observation, "I recently watched this video about running tailscale client in a docker container along side another service, which allows me to access the service using my tailscale dns," highlights how easy it is to integrate. You can run the Tailscale client right alongside another service in a Docker container, making that service accessible via your Tailscale network. This is incredibly useful for microservices or complex application deployments.
Automation is also a big plus for Tailscale. If you're looking to automate installations, like writing a Windows batch script, you might be trying to find ways to install it without prompts or graphical windows. This is a common need for system administrators, as I've experienced: "I'm writing a windows batch script to automate the installation process of tailscale, thus i need a way to install it without prompt and any graphical window and i'm struggle on." Tailscale generally provides options for silent installations, which is a definite advantage for large-scale deployments, as a matter of fact.
When running Tailscale in containers, you also need to consider user permissions. As noted, "When this is set, tailscale runs as a relatively random user, If unchecked, it runs as root and all is good, And of course you do want to check host network." This means understanding how permissions affect the client's operation and ensuring you configure the container with the necessary network access, usually by checking the "host network" option for full functionality, just to be safe.
Tailscale Funnel and Azure Services
Tailscale also offers unique features like Tailscale Funnel, which lets you serve websites or services from your private network directly to the public internet through a secure tunnel, without opening any firewall ports. My attempt to use it, "$ tailscale funnel index.html error:," shows that while it's a powerful feature, it might require some specific configuration to get right. This is a pretty advanced use case, but it's very convenient for sharing internal tools or demos.
When it comes to cloud integrations, like with Azure services, Tailscale has a different approach. As I've noted, "Since tailscale cannot be integrated directly with azure services, you would need to deploy it as a separate instance to act as a proxy to other services." This means you can't just 'turn on' Tailscale within Azure's native networking. Instead, you'd set up a Tailscale node within your Azure environment to act as a gateway or proxy, allowing your Tailscale network to reach your Azure resources. This, arguably, adds a layer of flexibility, even if it requires a bit more setup.
Performance Considerations
Both WireGuard and Tailscale are known for their excellent performance. WireGuard's protocol is lean and efficient, using modern cryptography that's optimized for speed. This means very low overhead, which translates to fast connection times and high throughput, which is very good.
Tailscale, being built on WireGuard, inherits this performance. Because it also tries to establish direct peer-to-peer connections whenever possible, your data often travels the most efficient path between devices, rather than bouncing through a central server. This "hole punching" capability helps maintain high speeds, even when devices are behind different firewalls or routers, just to make things clear. The only potential performance difference might come from the overhead of the coordination server during initial connection setup, but for ongoing data transfer, they are quite similar.
When to Choose WireGuard
You might lean towards WireGuard if you:
- Prefer a completely self-hosted solution with no reliance on third-party services, even for coordination.
- Have a deep understanding of networking and want granular control over every aspect of your VPN setup.
- Need to connect a small, fixed number of devices and don't mind manual configuration.
- Are building a custom network solution where WireGuard is a component, not the whole package.
- Prioritize the smallest possible attack surface and want to audit every line of code yourself.
When to Choose Tailscale

Tailscale vs WireGuard
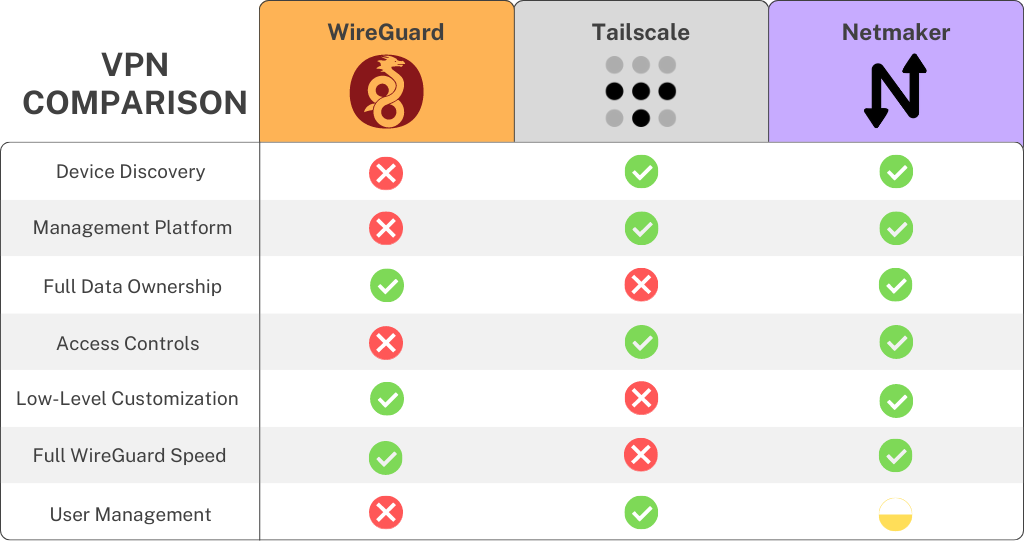
Tailscale vs WireGuard

Tailscale vs Wireguard: Implications for accessibility & security